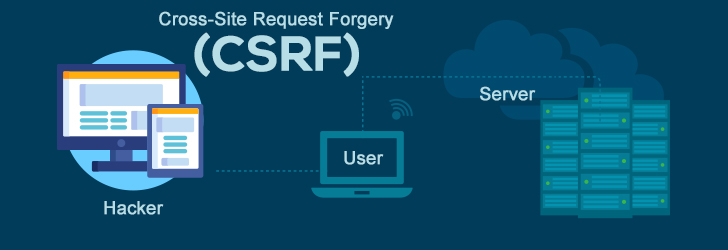
Firstly, we must define what a buffer is. A buffer is an allocated section of memory which can hold anything from a string of characters to an array of integers. That being the case, a buffer overflow (or overrun) is what happens a buffer with a fixed-length receives more data than what it can handle. In this case, the extra data has to be stored somewhere and spills over into an adjacent space in memory which can corrupt or overwrite the data stored there. These overflows usually result in a system crash; however, they also create opportunities for an attacker to run some malicious code or manipulate coding errors. The success of these attacks are very high as most programming languages, such as C, C++, and Fortran are vulnerable to these types of attacks.
[..]
Read more...