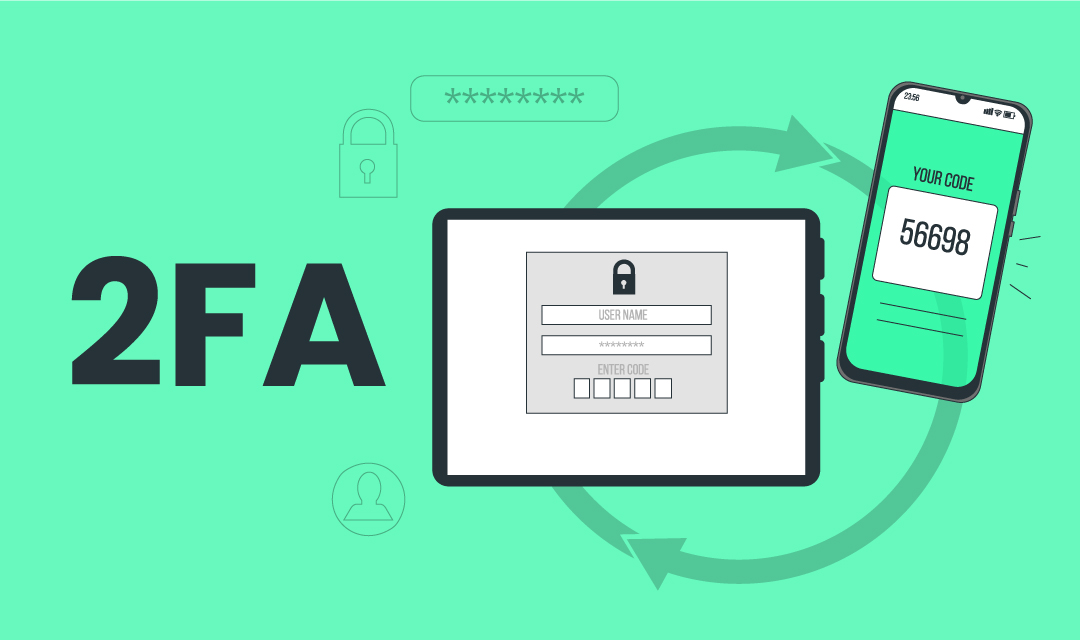
2FA (2-factor authentication) is a form of MFA where a user is required to supply 2 forms of authentication to allow access to the system. The traditional authentication system used the username/password pair to grant access to an account, but a growing number of hacking due to the use of weak passwords prompts the industry to offer an additional form of authentication to enhance the security of login access.









