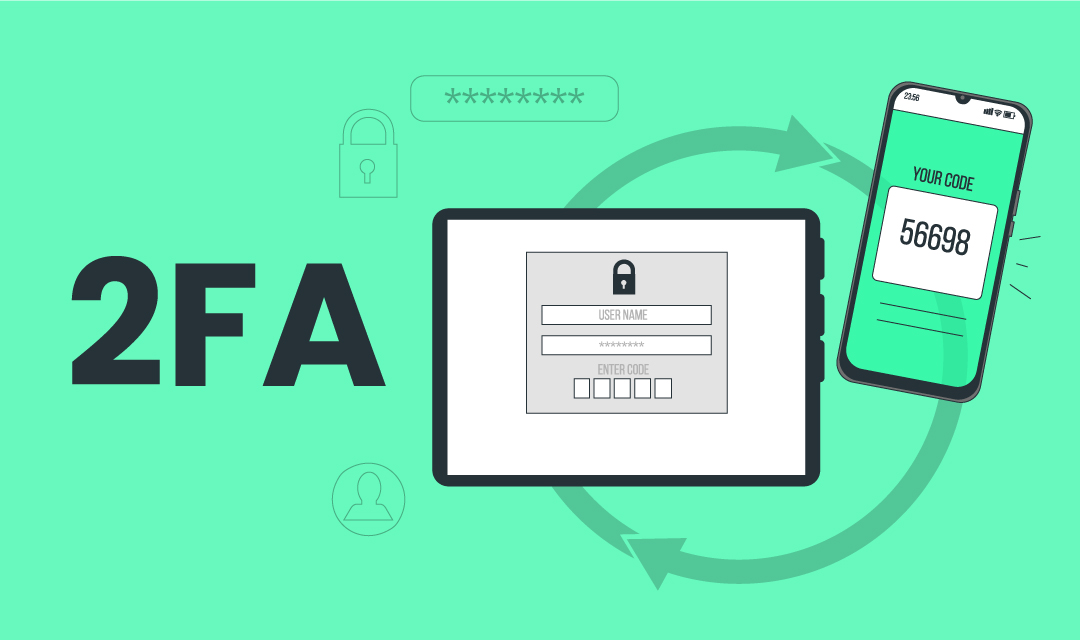
When COVID-19 was first discovered in 2019, most people thought their lives would remain unaffected by the outbreak, which eventually turned into a pandemic. Fast-forward to 2021 and most people that could work from home are doing so, and it is staying for the long haul.
The perks of working from home are numerous. You can roll out of bed in your pj’s and still make it on time for the Monday 9 am meeting. Having the comfort of your own home, avoiding the commute, saving money on those office lunches because you forgot your packed lunch…. I could go on. It’s not all perks though, as there are always thieves and scammers on the lookout and with most workers using their own devices and laptops, cybersecurity could range from financially devastating to easily avoidable.