Imagine your favorite website suddenly going down. You can’t access it, and neither can anyone else. This might be due to a Distributed Denial of Service (DDoS) attack. In recent years, DDoS attacks have surged dramatically. In 2024, Cloudflare reported mitigating nearly 6 million DDoS attacks in Q3 alone—a 49% increase from the previous quarter and a 55% rise year-over-year. This guide will help you understand DDoS attacks, how they work, their motivations, types, and mitigation strategies.
Understanding the Fundamentals of DDoS Attacks
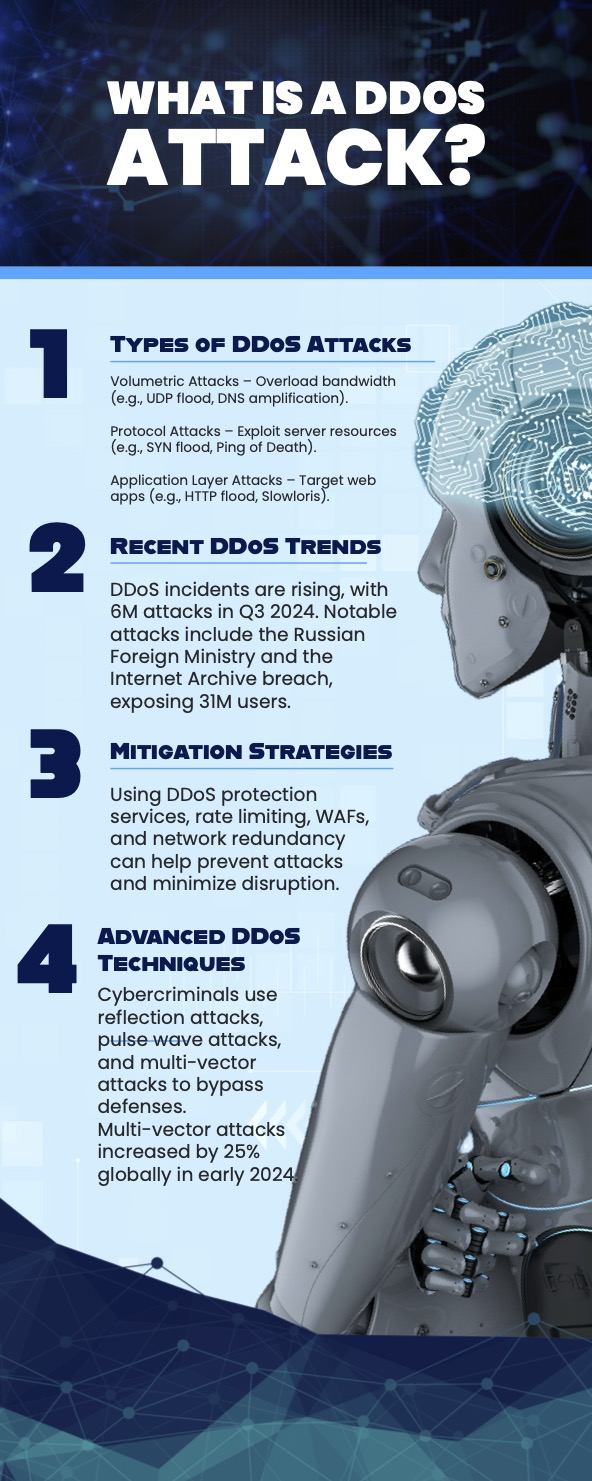
What is a DDoS Attack?
DDoS stands for Distributed Denial of Service. It occurs when multiple compromised devices flood a target system with overwhelming traffic, rendering it inaccessible. Unlike a standard DoS (Denial of Service) attack, which originates from a single source, DDoS attacks come from multiple sources, making them more potent and harder to mitigate.
How DDoS Attacks Work
DDoS attacks rely on botnets, which are networks of infected devices, including computers and IoT gadgets. Attackers infect these devices with malware, turning them into "bots" that follow the attacker’s commands. These bots then flood the target system with excessive requests, exhausting its resources and causing service disruptions.
Real-World Examples
DDoS attacks continue to pose significant threats to organizations worldwide, with recent incidents highlighting their evolving scale and complexity. Here are some notable examples:
- October 2024: Russian Foreign Ministry's website suffered an unprecedented DDoS attack during the BRICS summit, disrupting access and highlighting the increasing severity of such threats.
- October 2024: The Internet Archive suffered a major DDoS attack, exposing data of 31 million users. The hacktivist group SN_BlackMeta, linked to pro-Palestinian movements, claimed responsibility.
Cloudflare mitigated nearly 6 million DDoS attacks in Q3 of 2024, a 55% YoY increase.
Common Motivations Behind DDoS Attacks
- Extortion: Attackers demand payment to halt an attack.
- Competitive Advantage: Businesses may attempt to disrupt competitors’ online services.
- Hacktivism: Political or ideological groups launch DDoS attacks to protest organizations.
- Cyber Warfare: Nation-states use DDoS attacks to disrupt infrastructure in rival countries.
By understanding these threats and implementing robust security measures, businesses and individuals can better protect themselves from the devastating impact of DDoS attacks.

Types of DDoS Attacks
DDoS attacks come in various forms, each targeting different aspects of a system. Below are the primary types:
1. Volumetric Attacks: Overwhelming Bandwidth
These attacks flood the target’s bandwidth, preventing legitimate traffic from getting through. Examples include:
- UDP Flood Attacks
- Attackers send a massive number of UDP packets to random ports.
- The target system tries to respond, exhausting its resources.
- ICMP (Smurf) Attacks
- Attackers send spoofed ICMP requests to a broadcast address.
- All devices on the network respond to the target, overwhelming it with replies.
- DNS Amplification Attacks
- Attackers send small DNS requests with a spoofed source address.
- DNS servers respond with large data packets to the victim, amplifying the attack.
2. Protocol Attacks: Exploiting Server Resources
These attacks target server resources instead of bandwidth. Examples include:
- SYN Flood Attacks
- Exploit the TCP handshake process by sending excessive SYN requests.
- The target system waits for a response that never comes, depleting resources.
- Ping of Death Attacks
- Attackers send oversized ICMP packets.
- When the target reassembles them, it crashes due to buffer overflow.
- Fragmentation Attacks
- Attackers send fragmented packets that require extensive processing.
- Overwhelms the target’s ability to reassemble packets.

3. Application Layer Attacks: Targeting Web Applications
These attacks target specific applications rather than network infrastructure. They often mimic legitimate traffic, making them harder to detect.
- HTTP Flood Attacks
- Attackers generate excessive GET/POST requests.
- Servers become overloaded trying to process these requests.
- Slowloris Attacks
- Attackers open connections but send data very slowly.
- The server keeps these connections open, exhausting resources.
- Application-Specific Exploits
- Attackers exploit known vulnerabilities in applications like WordPress.
- This allows them to crash the application or gain unauthorized access.
Advanced DDoS Techniques
As cybersecurity improves, attackers develop more sophisticated methods to bypass defenses. Here are some advanced DDoS techniques:
Reflection Attacks
- Attackers send requests with a spoofed source IP to third-party servers.
- The servers send responses to the victim, amplifying the attack.
Pulse Wave Attacks
- Short, high-intensity bursts of traffic.
- Harder to detect as they do not maintain a continuous attack pattern.
Multi-Vector Attacks
- Combine different attack types to maximize damage.
- In early 2024, multi-vector attacks increased by 25% globally.

DDoS Mitigation Strategies
Protecting against DDoS attacks requires a multi-layered defense strategy. Here are some best practices:
- DDoS Protection Services
- Cloud-based services filter malicious traffic before it reaches the target.
- Providers like Cloudflare, Incapsula and Akamai offer robust DDoS protection.
- Rate Limiting and Traffic Shaping
- Controls the number of requests a user can make.
- Traffic shaping prioritizes critical requests.
- Web Application Firewalls (WAFs)
- Analyzes HTTP traffic and blocks malicious requests.
- Protects against application-layer attacks like HTTP floods.
- Network Redundancy and Scaling
- Deploy multiple servers in different locations.
- Distributes traffic to reduce the impact of an attack.
- Anycast Routing
- Routes incoming traffic to multiple locations.
- Prevents a single point of failure by distributing requests.
Conclusion
DDoS attacks are becoming more frequent and sophisticated. Attackers use various methods, from volumetric and protocol-based attacks to advanced multi-vector strategies. The motivations behind these attacks range from financial extortion to cyber warfare. Implementing strong security measures such as DDoS protection services, rate limiting, and web application firewalls is crucial. As threats evolve, staying informed and proactive is the best way to safeguard your online infrastructure.
Images by Freepik.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.


Comments (0)
No comment