
In today's age, ensuring network security is crucial. Each internet-connected device has its identifier called an IP address, which is essential for safeguarding your digital assets. How exactly do IP addresses enhance network security? What steps can you take to keep them safe? Let's explore the specifics.
Understanding IP Addresses
What is an IP Address?
An IP address, also known as an Internet Protocol address consists of a sequence of numbers separated by periods or colons. This identifier allows devices on a network to communicate with one another efficiently like a home address for your device.
Different Types of IP Addresses
IPv4
IPv4, the iteration of the Internet Protocol, utilizes a 32-bit addressing system that accommodates over 4 billion addresses. Despite its use, the surge in internet-connected devices has depleted IPv4 addresses.
IPv6
To overcome this scarcity issue, IPv6 was introduced. With a 128-bit addressing system, IPv6 offers nearly unlimited unique addresses. Alongside its expanded address space, IPv6 also brings security features into play.
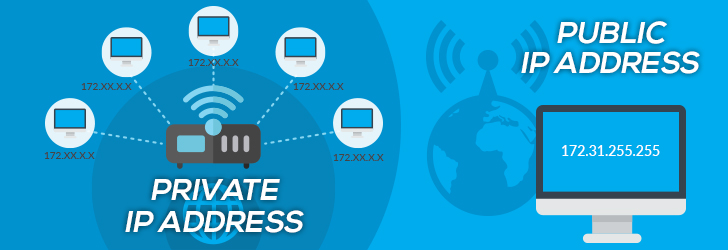
Differences Between Public and Private IP Addresses
Public IP addresses are given to your devices by your Internet Service Provider (ISP) and can be accessed over the Internet. Private IP addresses are utilized within a network, such as at home or in an office, and cannot be directly reached from outside sources.
Understanding How IP Addresses Function
The Process of Allocating IP Addresses
IP addresses are distributed by the Internet Assigned Numbers Authority (IANA) and Regional Internet Registries (RIR. When you connect to the internet, your ISP assigns an IP address to your router, which then assigns IP addresses to individual devices.
The Classification of IP Address Classes
IP addresses are classified into five groups (A, B, C, D and E) based on their support for networks and hosts. Classes A, B, and C are typically used for networking purposes; classes D and E are used for multicasting and experimental projects.
Breaking Down Subnetting and CIDR
Subnetting involves dividing a network into sub-networks, for improved security and efficiency. Classless Inter Domain Routing (CIDR) further enhances the allocation of IP addresses by allowing address space utilization.
The Significance of IP Addresses in Safeguarding Networks
Device Identification
IP addresses play a role in identifying devices within a network. This identification is key for network administrators to manage devices effectively and ensure that authorized ones can connect to the network.
Monitoring Activities
By tracking IP address activities, administrators can monitor network traffic, spot patterns, and delve into behaviors. Such monitoring is vital for spotting security risks and taking action.
Regulating Access
IP addresses control access to network resources. Administrators can set up firewalls and access control lists (ACLs) to allow or block traffic based on IP addresses, thereby strengthening the network's security.
Common Threats Associated with IP Addresses
IP Spoofing
In IP spoofing, attackers alter their device's IP address to pretend to be another device. This deceptive tactic is often employed in cyberattacks like session hijacking and network reconnaissance attempts.
DDoS Attacks
Distributed Denial of Service (DDoS) attacks flood a targeted server with data from sources frequently using forged IP addresses. These attacks can potentially disrupt network services, making them inaccessible to legitimate users.
Man in the Middle Attacks
In Man in the Middle (MitM) attacks, hackers modify communication between two parties by exploiting weaknesses in how IP addresses are handled. This situation could result in data breaches and unauthorized access to information.
Best Practices for Safeguarding IP Addresses
Deploying Firewalls
Firewalls serve as a shield between your network and external dangers. You can prevent traffic and safeguard your network by setting up firewalls to screen traffic based on IP addresses.
Utilizing VPNs
Virtual Private Networks (VPNs) encrypt your internet connection concealing your IP address and ensuring the confidentiality of your activities. This proves valuable when accessing data on public networks.
Regular System Updates and Patching
Ensuring that your systems and software are regularly updated is essential for minimizing security risks. Routine updates and patches help defend against vulnerabilities that could jeopardize your IP addresses and network security.
Advanced Security Strategies for IP Addresses
IP Whitelisting and Blacklisting
Whitelisting permits only trusted IP addresses to access your network while blacklisting blocks known IP addresses. These methods offer a layer of security guaranteeing that authorized users can connect.
Intrusion Detection Systems (IDS)
IDS monitors network traffic for behavior and potential threats. By examining patterns and actions related to IP addresses, IDS can notify administrators of security incidents, facilitating a response.
IP Tracking and Personal Security
IP tracking is a method used to monitor and gather information about internet users based on their IP addresses. IP tracking can provide an approximate geographic location of a user and allows network administrators to monitor the user's online activities, identify patterns, and detect suspicious behavior.
While IP addresses are crucial for network security, they are insufficient for tracking or spying on someone's personal activities. IP addresses only indicate the device's general location and connection point to the internet. They do not reveal specific activities or communications of the user. For more comprehensive monitoring techniques, and incorporating advanced tools, you may visit here for more information.
Future of IP Address and Network Security
Emerging Technologies
Blockchain and artificial intelligence (AI) are poised to revolutionize IP address security. Blockchain can provide transparent and tamper-proof IP address management, while AI can enhance threat detection and response capabilities.
Predictions and Trends
As the number of connected devices grows, the demand for advanced IP address security solutions will increase. Future trends may include the widespread adoption of IPv6, improved encryption methods, and more sophisticated intrusion detection systems.
Conclusion
IP addresses are fundamental to network security, serving as unique identifiers that enable device communication and access control. By understanding their role and implementing best practices, you can protect your digital assets from a myriad of threats. Regularly updating your systems, utilizing advanced security techniques, and managing your IP addresses effectively are essential steps in safeguarding your network.
 FAQs
FAQs
An IP address is a unique identifier assigned to each device connected to a network, allowing them to communicate with one another. It is crucial for network management and security.
Protect your IP address by using firewalls, VPNs, regularly updating your systems, and implementing IP whitelisting and blacklisting.
IPv6 offers enhanced security features compared to IPv4, including built-in IPsec support, which provides data integrity, authentication, and encryption.
IP spoofing involves attackers disguising their IP address to impersonate another device. Prevent it by using firewalls, IDS, and secure DNS practices.
IP Address Management (IPAM) is crucial for maintaining organized and secure networks by managing IP address allocation, usage, and conflicts, reducing the risk of security breaches.
Related Posts
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.


Comments (0)
No comment