
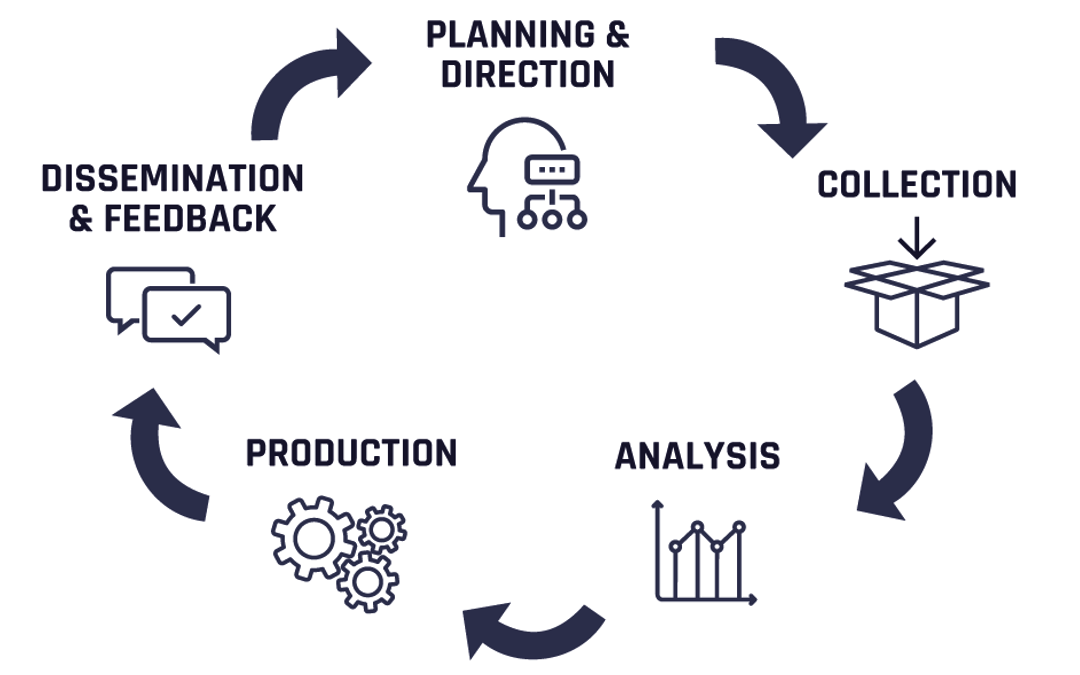
In an era where cyber threats evolve rapidly, establishments must adopt a proactive approach to safeguard their digital assets. The Cyberthreat Intelligence lifecycle is a scientific system designed to convert raw data into actionable insights, enabling organizations to preempt and counter cyber threats effectively. This lifestyle cycle contains six distinct and iterative stages: Direction, Collection, Processing, Analysis, Dissemination, and Feedback. Each stage performs a crucial role in enhancing the overall cybersecurity posture.
1. Direction
The first stage includes defining the objectives and requirements for the threat intelligence program. This stage sets the foundation for the entire lifecycle by identifying what information is wanted and why. It requires collaboration between various stakeholders, such as the security team, executives, and other relevant departments, to ensure that the intelligence efforts align with the organization's strategic goals.
Key activities:
- Identifying critical assets and potential threats
- Establishing intelligence requirements
- Prioritizing intelligence needs based on risk assessment
2. Collection
Once the direction is established, the collection stage makes a specialty of amassing relevant statistics from numerous sources. This data can come from internal sources inclusive of logs and network traffic, as well external sources like threat feeds, open-source intelligence (OSINT), and dark web monitoring. The goal is to acquire as a good deal of relevant information as possible to build a comprehensive threat landscape.
Key activities:
- Leveraging automated tools to acquire data
- Monitoring threat intelligence feeds
- Collecting data from social media, forums, and different online platforms
3. Processing
Raw data collected in the previous stage could be more structured and voluminous. The Processing stage involves organizing and structuring this data to make it usable for evaluation. This includes filtering out irrelevant facts, normalizing data formats, and enriching data with extra context.
Key activities:
- Data cleaning and normalization
- Enriching records with contextual information
- Storing processed data in a centralized repository
4. Analysis
In the analysis stage, processed data is scrutinized to identify patterns, trends, and anomalies. This stage transforms records into actionable intelligence by applying various analytical techniques, including machine learning, behavioral analysis, and correlation with historical data. The goal is to generate insights that may inform decision-making and response strategies.
Key activities:
- Identifying indicators of compromise (IOCs)
- Correlating data to detect threat patterns
- Generating Threat reports and risk assessments
5. Dissemination
The Dissemination degree involves distributing the analyzed intelligence to relevant stakeholders. This may include security teams, management, and external partners. Effective dissemination ensures that the right people receive the right information at the right time, enabling timely and informed actions.
Key activities:
- Creating and distributing intelligence reports
- Sharing information with external partners and information-sharing communities
- Providing actionable recommendations based on the analysis
6. Feedback
The final stage, feedback, is crucial for refining and improving the threat intelligence lifecycle. This stage involves collecting feedback from stakeholders on the application and effectiveness of the disseminated intelligence. it also includes reviewing and updating the intelligence requirements based on the evolving threat landscape and organizational needs.
Key activities:
- Gathering Feedback from stakeholders
- Assessing the effectiveness of intelligence products
- Updating intelligence requirements and priorities
Conclusion
The threat intelligence lifecycle is a continuous and dynamic process that enables organizations to stay ahead of cyber threats. by systematically moving from direction to feedback, the Organization can transform raw data into actionable insights that drive informed decision-making and effective threat mitigation. Understanding and optimizing each of the six levels is essential for building a robust threat intelligence capability that enhances overall cybersecurity resilience.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.


Comments (0)
No comment