
Home networks have evolved dramatically over the past two decades. What started as a single computer connected to a dial-up modem has transformed into complex networks handling multiple devices and services. Modern homes now typically connect 15-20 devices simultaneously - from laptops and smartphones to smart TVs and security systems. Effective network management has become essential with the increasing demands of 4K streaming, remote work, and smart home devices. This is where private IP addressing proves invaluable.
Understanding Private IP Addressing
Private IP addressing is more than just a way to connect devices - it's fundamental to network management and security. Recent testing by network engineers at “Router’s Network Admin” demonstrates how private IP addressing provides the foundation for both network organization and security implementation.
The Internet Assigned Numbers Authority (IANA) has designated specific ranges for private networks:
Class A: 10.0.0.0 to 10.255.255.255 (16,777,216 addresses) 172.16.0.0 to 172.31.255.255 (1,048,576 addresses) Class C: 192.168.0.0 to 192.168.255.255 (65,536 addresses)
Most home networks utilize Class C addresses, typically beginning with 192.168, as this provides an ideal balance between manageability and available addresses. For larger networks or specific requirements, Class A or B ranges offer more flexibility.
Network Segmentation Strategies
Modern home networks benefit from proper segmentation. This approach improves security, simplifies management, and optimizes performance. The following diagram illustrates a typical segmentation setup:
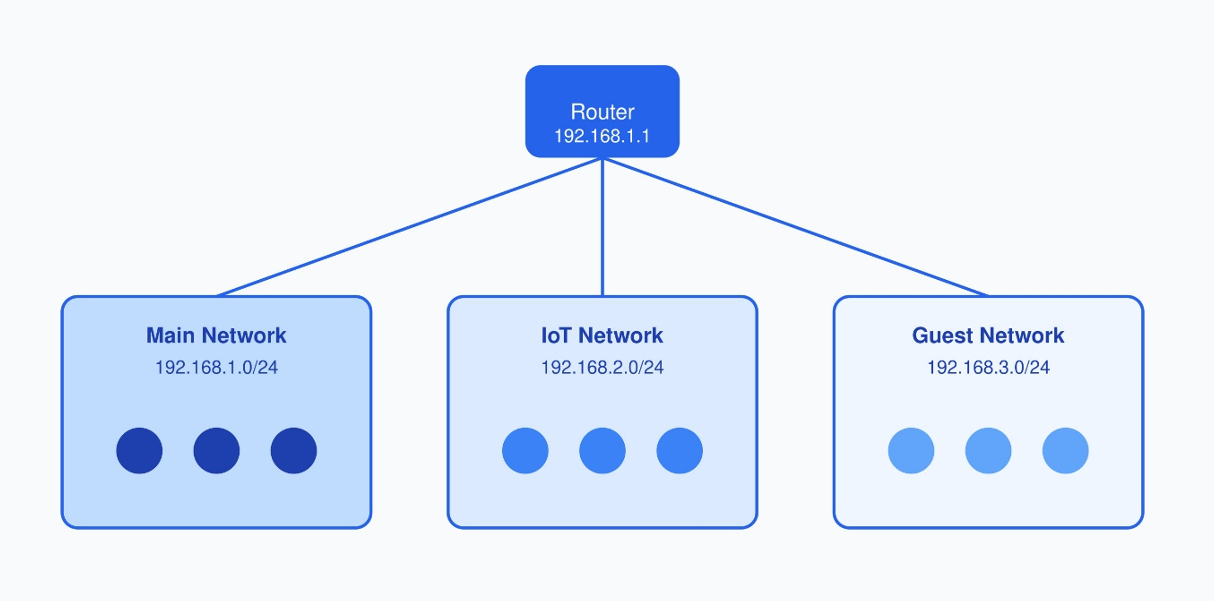
As shown in the diagram above, a well-structured home network typically consists of three main segments, each serving different purposes and requiring specific security considerations. Let's look at the detailed implementation:
Main Network (192.168.1.0/24)
This segment handles primary devices and critical services.
Router Configuration: Primary Interface: 192.168.1.1 Subnet Mask: 255.255.255.0 DHCP Range: 192.168.1.100-192.168.1.200 Reserved Range: 192.168.1.2-192.168.1.99 (for static assignments) DNS Servers: Custom or ISP provided Gateway: 192.168.1.1
The main network requires robust security and reliable performance. Static IP assignments in the reserved range work well for:
- Network storage devices
- Printers
- Media servers
- Gaming consoles requiring port forwarding
IoT Network (192.168.2.0/24)
Smart home devices benefit from isolation while maintaining necessary connectivity.
IoT Segment Configuration: Interface: 192.168.2.1 DHCP: 192.168.2.100-192.168.2.200 mDNS: Enabled for device discovery Multicast: Allowed for device communication Security: Isolated from main network
This segregation provides several advantages:
- Limits potential security breaches
- Controls IoT device access
- Simplifies device management
- Enables specific traffic rules
Guest Network (192.168.3.0/24)
A dedicated guest segment provides internet access while protecting your main network.
Guest Network Settings: Interface: 192.168.3.1 DHCP: 192.168.3.100-192.168.3.200 Access: Internet only Client Isolation: Enabled Bandwidth Limit: 50% of total
Security Implementation
Network security requires multiple layers of protection. Here's how to implement comprehensive security:
Firewall Configuration
Essential firewall rules protect network segments while allowing necessary traffic:
# Protect main network from IoT devices iptables -A FORWARD -i eth0 -o eth1 -s 192.168.2.0/24 -d 192.168.1.0/24 -j DROP # Isolate guest network iptables -A FORWARD -i eth0 -o eth1 -s 192.168.3.0/24 -d 192.168.1.0/24 -j DROP # Allow specific management access iptables -A FORWARD -i eth0 -o eth1 -s 192.168.1.10 -d 192.168.2.0/24 -j ACCEPT # Rate limit guest network iptables -A FORWARD -s 192.168.3.0/24 -m limit --limit 10/second -j ACCEPT
These rules establish:
- Segment isolation
- Controlled access paths
- Rate limiting for guests
- Management capabilities
Authentication Methods
Implement strong authentication across the network:
- WPA3 Enterprise where supported
- MAC address filtering with automated updates
- RADIUS integration for enhanced control
- Certificate-based authentication for critical systems
Performance Optimization
QoS Configuration
Quality of Service ensures critical applications get necessary resources. The following diagram illustrates how bandwidth is typically allocated across different traffic types:

Based on this prioritization model, here's the detailed configuration:
High Priority Traffic: Bandwidth: 70% minimum Latency Target: Under 20ms DSCP Marking: EF (46) Applications: Video calls, gaming Queue: Strict Priority
Standard Traffic: Bandwidth: 20% minimum Latency Target: Under 100ms DSCP Marking: AF31 (26) Applications: Web, email Queue: Weighted Fair
Background Traffic: Bandwidth: Remaining No latency guarantee DSCP Marking: BE (0) Applications: Updates, downloads Queue: Best Effort
This QoS implementation ensures:
- Critical applications perform reliably
- Regular browsing remains responsive
- Background tasks don't interfere with important activities
Troubleshooting Common Issues
When problems arise, systematic troubleshooting helps identify and resolve issues quickly.
Smart Device Connectivity
Common problems and solutions:
Issue: Devices disconnecting Check: 1. DHCP lease times (increase if too short) 2. Signal strength (improve AP placement) 3. Channel congestion (select less busy channels) 4. IP conflicts (verify DHCP ranges)
Gaming Optimization
Improve gaming performance:
Steps: 1. Enable UPnP or configure port forwarding 2. Verify NAT type (aim for Open or Type 2) 3. Monitor latency and packet loss 4. Configure QoS priorities
Planning for IPv6
While IPv4 private addressing works well, IPv6 preparation ensures future compatibility.
Address Structure
IPv6 Planning: Global Prefix: 2001:db8::/48 (example) ULA Prefix: fd00::/8 Subnet Size: /64 Interface IDs: EUI-64 or random
Implementation Steps
- Enable dual-stack operation
- Configure DHCPv6 services
- Implement security measures
- Test application compatibility
Network Management Best Practices
Effective network management combines monitoring, maintenance, and documentation.
Monitoring Configuration
Essential Metrics: Bandwidth utilization Connection states Error rates Security events Device status
Regular Maintenance
Maintain network health through:
- Regular firmware updates
- Security patch management
- Configuration backups
- Performance optimization
- Security audits
Conclusion
Private IP addressing provides the foundation for efficient home network management. Through proper implementation of segmentation, security measures, and performance optimization, home networks can deliver reliable service for diverse applications. Regular monitoring and maintenance ensure the network continues to meet evolving requirements.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.

Comments (0)
No comment