Online scams are on the rise, with fraudsters increasingly targeting unsuspecting website owners to exploit their platforms for financial gain. These scammers often impersonate representatives of reputable media brands, presenting enticing offers for guest posts, sponsored content, or backlinks to build trust and gain access.
In recent months, we’ve received several deceptive emails from various Gmail accounts impersonating a manager at Mashable. These messages offered $1,200 per month in exchange for displaying a so-called “Mashable Footer” on our website. Since we regularly receive advertising inquiries, we reviewed the proposal carefully—but a few suspicious details in the email raised red flags.
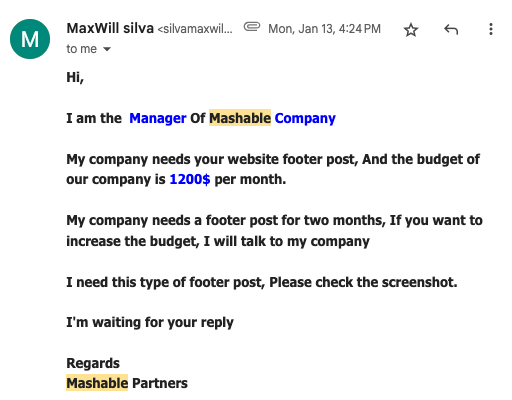
- Although the sender claims to represent Mashable, the email was sent from a Gmail address. This is highly suspicious, especially since the individual identifies themselves as a manager at Mashable. Also, we received at least 4 identical emails from 4 different individuals, "Clane Chughes", "Julian Hazel", "Jessica Amelia", and "MaxWill silva".
- The requested footer post contains the message: "Mashable is a global company, multi-platform media and entertainment company. For more queries and news contact us at this email: mashablepartners@gmail.com." This message is written from Mashable’s perspective, implying that we are Mashable, which is a major red flag.
- We received the exact same email on two of our websites, with identical offers, despite the significant differences in traffic statistics. This further indicates the offer is not legitimate.
As part of our mission to educate readers about online scams, we decided to investigate further by replying to the sender regarding point #2 above. We specifically asked about the intent behind the message. Instead of addressing our question, the individual ignored it and simply instructed us to place the footer post and send an invoice after the placement.
We continued asking questions to other individuals, but the responses remained the same—complete disregard and avoidance.
How the Scam Operates
Scammers initiate contact via email, posing as Mashable managers with subject lines like “I would also like to know the cost of publishing one article”, or “Inquiry About Paid Guest Posting”. They propose offering $1,200 per month for placing a footer on the victim’s website. Here is the screenshot of the "Footer Post" we received from one individual.

It’s clear that these fraudsters have no intention of paying the invoice once the footer post goes live. Their real objective is to use the footer as bait—luring victims into purchasing guest article placements or banner ads on Mashable at unrealistically low prices, often requiring upfront payment. By misusing the Mashable brand, they aim to deceive victims into thinking they’re engaging in legitimate advertising deals.
Protective Measures
To safeguard your company from falling victim of online scams:
- Verify Communications: Cross-reference any suspicious emails by contacting the company directly through official channels.
- Avoid Sharing Sensitive Information: Refrain from providing personal or financial details to unverified sources.
- Educate Your Team: Ensure that all team members are aware of such scams and understand the importance of scrutinizing unsolicited offers.
Conclusion
The Mashable Footer Post Scam serves as a stark reminder of the importance of vigilance in the digital realm. By staying informed and cautious, website owners can protect themselves from falling victim to such fraudulent schemes. Always prioritize verification and trust your instincts when confronted with unsolicited proposals.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.

Comments (0)
No comment