
Container escape is when an attacker breaks out of a containerized environment and gets access to the host system. Usually, containers are designed to keep these applications separate from each other and the main computer. So if one container is hacked, it shouldn’t harm the host system or other containers.
But if an attacker succeeds in escaping a container, he can access the main system and potentially cause a lot of damage or steal sensitive information. That’s why, it’s very important to understand and prevent container escape when it comes to effectively maintaining a strategy for securing, containing, and protecting your systems.
The problem with container escape
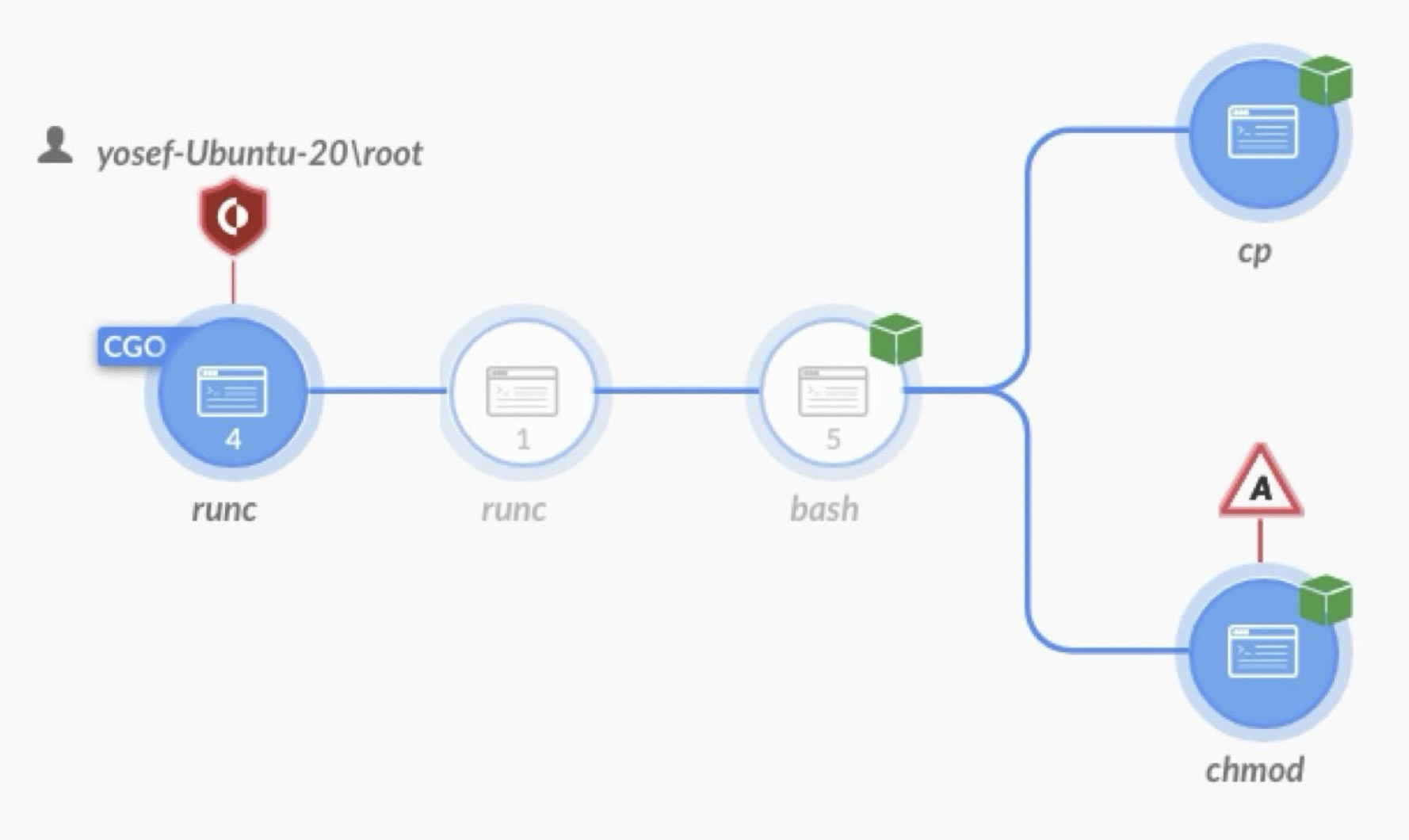
The main problem which comes with the container escape is that it can lead to severe security breaches. Containers are normally supposed to isolate applications, but when this isolation breaks, attackers can access sensitive data, change system configurations, or run malicious code on the host machine.
What happens if container security is compromised, let’s read it!
- Loss of data
- Compromise of other containers
- Control of the entire system by attackers
- Breaches that spread across different environments (development, testing, production)
In short, container cybersecurity is greatly affected when container escape exploits occur.
How container escape occurs?
Container escape occurs when attackers find and exploit vulnerabilities in the container environment. These vulnerabilities often exist in the container’s configuration, runtime, or the software it is using.
Here are some common ways by which attackers can break out of containers:
- Misconfigured containers: If containers are set up with weak or incorrect configurations, they might fail to keep proper isolation between the container and the host system.
- Kernel vulnerabilities: Containers share the same kernel as the host system. If there is a vulnerability in the kernel, then attackers can easily exploit it to gain access to the host.
- Unpatched software: If there is outdated software running inside the container or on the host system, it can contain vulnerabilities that attackers can use for container escape.
- Privileged containers: If the container is running with too many permissions, it gives them access to parts of the host system they shouldn’t have. This makes it easier for attackers to escape.
Container escape vulnerability examples
Here are a few notable examples of container escape vulnerabilities:
- Dirty Cow (CVE-2016-5195) This is a kernel vulnerability that allows attackers to gain more control than they should have.
- CVE-2019-5736 This vulnerability affected Docker and allowed attackers to run harmful code on the host machine by overwriting the parts of the host’s file system.
- RunC vulnerability RunC, a basic program that manages containers, had a vulnerability that could let an attacker gain full control (root access) of the host machine.
All these examples highlight why it is very important to secure and protect containerized environments.
How to prevent and detect container escape?
You need to follow the best practices to prevent and detect container escape:
Prevention strategies
- Use proper container configuration: You have to make sure that the containers are set up with the correct security settings. Also, try to avoid using privileged containers unless when very necessary.
- Regularly patch and update systems: Keep both the host system and containerized applications up to date. Because this way you can reduce the risk of known vulnerabilities being exploited.
- Implement the least privilege principle: Limit the permissions and access rights of containers to only what they need to operate. This reduces the potential damage if an attacker manages to escape from a container.
- Isolate containers: Use namespaces and control groups (cgroups) to limit what resources containers can access.
- Use container security tools: Use tools that are specifically designed to enhance container security such as Docker Bench or Kubernetes security policies.
- Enable container monitoring: Monitor your containers in real-time to detect any suspicious activities.
Detection strategies
- Regular security audits: Conduct regular audits of your container infrastructure to make sure that everything is secure.
- Use intrusion detection systems (IDS): Deploy IDS tools specifically for containers to detect any unusual behavior inside or outside the container.
- Implement runtime security: Runtime security tools can monitor containers while they're running and alert you to any unusual behavior or block them. This helps identify attempts to escape from a container.
 FAQs
FAQs
Suppose there are any vulnerabilities found in the configuration, software due to outdated, or the shared kernel between the container. In that case, the attacker takes advantage of this and then exploits the container easily.
You can spot container escape by watching the logs that record system activities with the help of special tools called intrusion detection systems. It alerts you to suspicious actions and looks for any strange behavior in the system. For example, if something unexpected happens, like a container trying to access resources it shouldn’t, these methods can help you catch it early.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.

Comments (0)
No comment