
Introduction: The Rise of OTPs in a Digital World
In today's online environment, trust is hard to come by. With the surge in cybercrimes, using strong security measures is essential. One-Time Passwords, or OTPs, have become a key player in enhancing security for online transactions and accounts.
OTPs offer an extra layer of protection by ensuring that only the person who has access to the OTP can enter a system or complete a transaction. This makes them a popular choice among users and businesses alike, especially for secure remote access. As more services adopt OTPs, they are reshaping how we interact online.
How One-Time Passwords Work: The Technology Behind the Scenes
Understanding the OTP Generation Process
OTPs are generated using a simple yet effective process. When a user initiates a login or transaction, the system generates a unique password. This password is used just once, meaning it expires quickly, usually within minutes.
Different OTP Algorithms and Their Security Levels
Several algorithms are used to generate OTPs. Some of the most common include:
- HOTP (HMAC-based One-Time Password): This generates a password based on a counter. OTP and HOTP are both ensuring safe password usage, OTPs are temporary passwords valid for a single session or transaction, while HOTP (HMAC-Based One-Time Password) generates a unique password using a cryptographic hash function and each time the counter increases, ensuring security with each use.
- TOTP (Time-Based One-Time Password): This uses the current time as a variable. The password is valid for a short window.
Both methods provide solid security, but TOTP is often preferred due to its time sensitivity.
Common OTP Delivery Methods
OTPs can be delivered through various channels:
- SMS: The OTP is sent directly to the user's mobile phone.
- Email: Users receive their OTP via email, although this may be less secure.
- Authenticator Apps: Apps like Google Authenticator generate OTPs directly on the user's device, providing more security than SMS.
Types of One-Time Passwords: A Detailed Breakdown

Time-Based OTPs (TOTP) Explained With Examples
TOTP is a popular method due to its time-sensitive nature. For instance, a user logs into their bank account, and a TOTP is generated that is valid only for 30 seconds. This makes it difficult for hackers to use outdated passwords.
Hardware-Based OTPs: Security Tokens and Their Applications
Hardware tokens are physical devices that generate an OTP. These are often used in high-security environments. For example, a company might provide its employees with Yubikey token that change the password every minute.
Event-Based OTPs and Their Use Cases
Event-based OTPs trigger based on a specific event, such as an attempt to access a secure file. These can be less common but are useful for unique access situations.
Benefits of Using One-Time Passwords for Enhanced Security
Increased Security Against Phishing and Hacking Attempts
Using OTPs significantly reduces the chances of unauthorized access. Even if a hacker gets hold of a password, they cannot log in without the OTP.
Compliance with Industry Regulations and Data Protection Laws
OTPs help businesses comply with data protection laws such as GDPR and PCI DSS. Ensuring secure access is critical for protecting user data and privacy.
Improved Account Protection and Reduced Fraud
With OTPs, fraudulent activities become tougher. They act as a barrier against account takeover attempts and unauthorized transactions.
Potential Drawbacks and Limitations of OTPs
The Risk of SIM Swapping and Social Engineering Attacks
Despite their advantages, OTPs are not foolproof. Hackers can use social engineering to get a user's phone number, allowing them to receive OTPs meant for someone else.
Challenges in Managing and Remembering Multiple OTPs
Users often have multiple accounts requiring OTPs, which can be overwhelming. This can lead to confusion and missed logins.
Dependence on Network Connectivity for Delivery Methods
Since many OTP methods rely on internet or phone service, users in areas with poor connectivity may have trouble receiving their codes.
Best Practices for Secure OTP Implementation and Usage

Choosing a Reliable OTP Provider and Authentication Method
Selecting a trustworthy provider is crucial. Evaluate vendors based on their security measures and technology.
Implementing Multi-Factor Authentication (MFA) for Maximum Security
Combining OTPs with other security methods, like biometrics, can drastically enhance protection.
Staying Informed About the Latest OTP Security Threats and Best Practices
Staying updated on current threats helps users adapt and protect their accounts effectively.
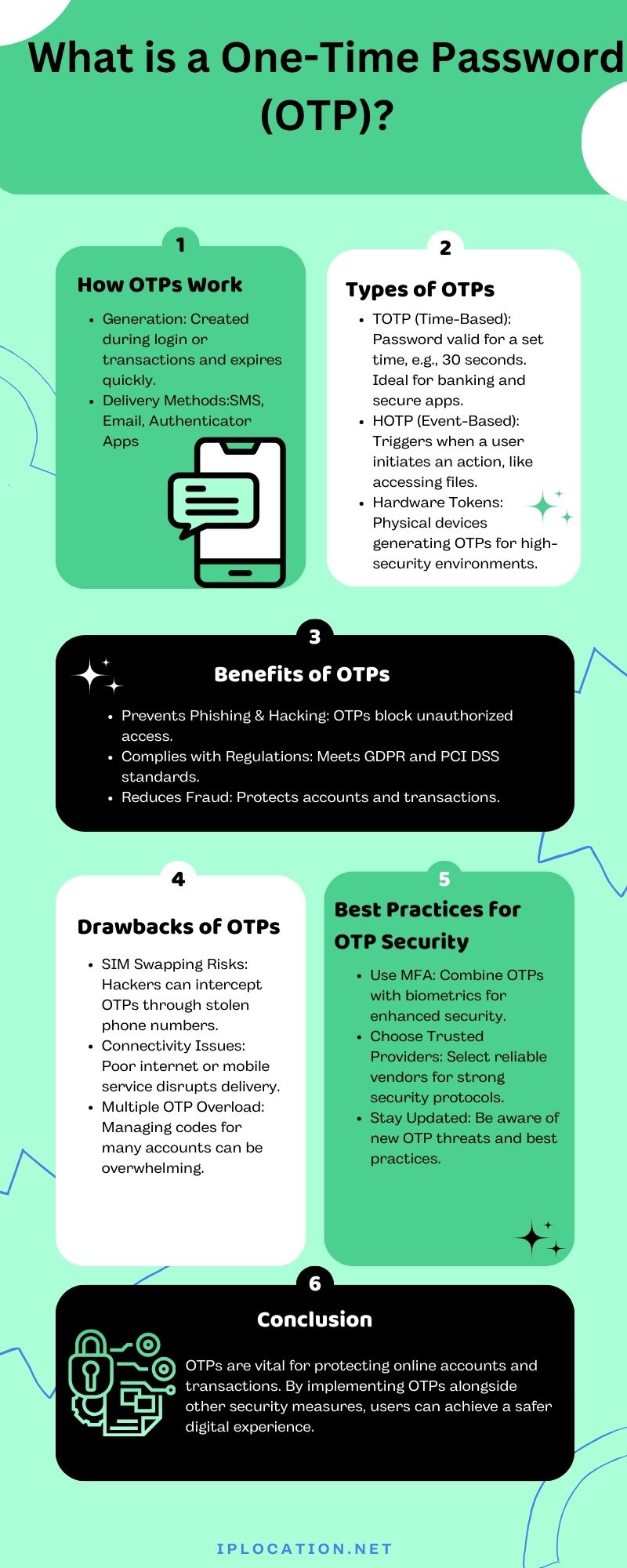
Conclusion: Embracing OTPs for a Safer Digital Future
OTPs are vital for secure online interactions. They provide an effective method for safeguarding sensitive information. In the future, we can expect OTP technologies to evolve, possibly incorporating biometric methods for even greater security. Adopting stronger security measures, including OTPs, is essential for anyone using online services. By staying vigilant and informed, we can enjoy a safer digital experience.
Images by Freepik
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.



Comments (0)
No comment