In today's rapidly evolving threat landscape, traditional perimeter-based security models are no longer sufficient to protect modern distributed networks and cloud environments.
Zero Trust Network Access (ZTNA) is an emerging cybersecurity paradigm that challenges the traditional perimeter-based approach to network security. In a ZTNA model, no user or device is inherently trusted, regardless of their network location or ownership. Instead, every access request is verified, authenticated, and continuously monitored, ensuring that only authorized entities can access specific resources based on a strict need-to-know principle.
This blog aims to explore the core principles of ZTNA, its logical components, and potential implementation strategies for organizations seeking to enhance their security posture and mitigate the risks associated with data breaches and lateral movement within their networks.
Core Principles of Zero Trust
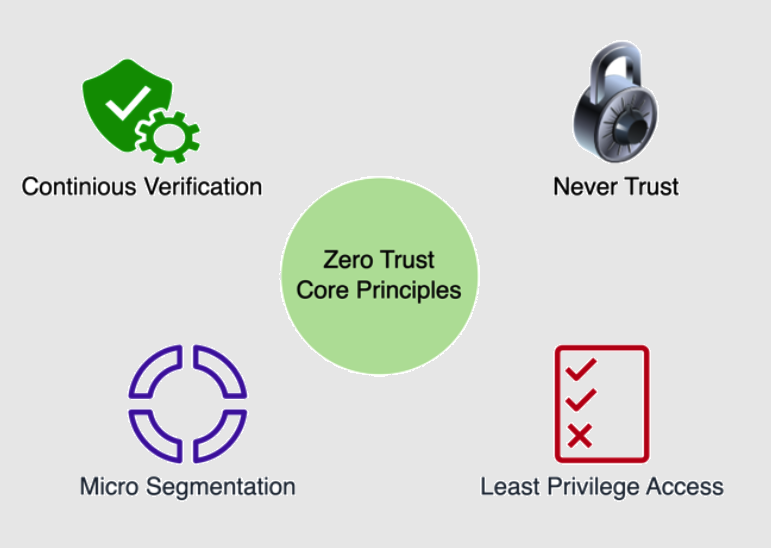
- Never Trust, Always Verify: The foundational principle of Zero Trust is to treat every access request as if it originates from an untrusted network. This applies to both external and internal users and devices.
- Least Privilege Access: Users and systems should be granted the minimum level of access required to perform their functions, reducing the potential attack surface.
- Micro segmentation: Network segments should be as granular as possible, limiting lateral movement in case of a breach.
- Continuous Monitoring and Validation: Trust is continuously evaluated and not assumed to persist once granted.
NIST SP 800-207
NIST Special Publication 800-207, titled "Zero Trust Architecture," provides a comprehensive overview and guidance on implementing the zero-trust security model within enterprise environments. This publication, developed by the National Institute of Standards and Technology (NIST), offers a detailed examination of the core tenets of zero trust, the logical components that comprise a zero-trust architecture (ZTA).
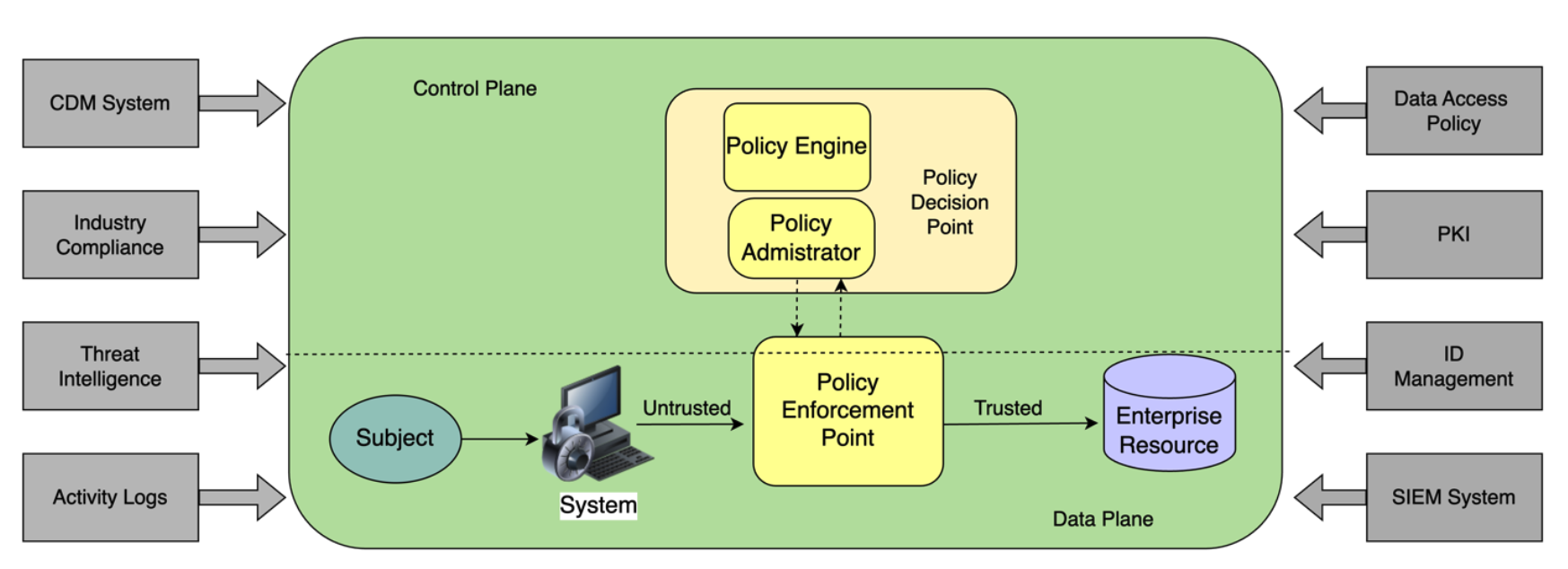
The NIST framework outlines several key logical components for implementing Zero Trust:
- Policy Engine (PE): The central decision point for access requests. It uses enterprise policy and external sources to make and log access decisions.
- Policy Administrator (PA): Responsible for establishing and/or terminating the communication path between a subject and a resource.
- Policy Enforcement Point (PEP): The system that ultimately enforces PE decisions on resource access.
Implementation Strategy
Migrating to a Zero Trust Architecture (ZTA) is an incremental journey rather than a complete overhaul of existing infrastructure. NIST recommends that organizations seek to progressively implement zero trust principles, process changes, and technology solutions that protect their most critical data assets and business functions.
1. Define the Protect Surface:
Begin by identifying your organization's most critical data, assets, applications, and services (DAAS). This forms your "protect surface" and is typically much smaller than the overall attack surface.
2. Map Transaction Flows:
Understand how traffic moves across your network in relation to your protected surface. This step is crucial for determining how to architect controls and enforce policy.
3. Architect the Zero Trust Network:
Design your network architecture with Zero Trust principles in mind. This often involves:
- Implementing Next-Generation Firewalls (NGFWs) as Segmentation Gateways
- Utilizing Software-Defined Networking (SDN) for dynamic micro segmentation
- Deploying a robust Identity and Access Management (IAM) system
4. Create Zero Trust Policies:
Develop granular policies using the Kipling Method (Who, What, When, Where, Why, and How) to define access rules. These policies should be based on the principle of least privilege and consider:
- User/device identity
- Application context
- Request time and location
- Data sensitivity
- Risk/threat intelligence
5. Monitor and Maintain the Network:
Implement continuous monitoring and logging of all traffic, focusing on:
- Real-time visibility into network traffic
- Behavioral analytics to detect anomalies
- Regular policy reviews and updates
- Integration with Security Information and Event Management (SIEM) systems
6. Initial Deployment and Monitoring:
Deploy the chosen ZTA components in a reporting-only mode to establish baseline activity patterns, refine policies, and ensure effective operations.
7. Expand ZTA Implementation:
Once sufficient confidence is gained, transition to steady-state operations and progressively expand the ZTA implementation to include additional business processes.
NIST emphasizes that most enterprises will operate in a hybrid ZTA/perimeter-based mode during the transition period, continuously investing in IT modernization initiatives to align with zero trust principles. Regular assessments and policy adjustments are necessary to adapt to changes in the enterprise's business processes, assets, and emerging threats.
Aligning with NIST External Components
To enhance the effectiveness of a Zero Trust Architecture (ZTA) implementation, organizations should integrate and leverage the following external components as outlined by NIST in SP 800-207:
Continuous Diagnostics and Mitigation (CDM) System:
A robust CDM system is crucial for monitoring the security posture of enterprise assets, including their software versions, patch levels, and the presence of vulnerabilities or unauthorized components. The CDM system provides the Policy Engine with real-time information about the assets involved in access requests, enabling informed decision-making based on their current state.
Industry Compliance Systems:
Organizations should integrate industry compliance systems to ensure that their ZTA implementation adheres to relevant regulatory regimes, such as FISMA, HIPAA, or financial industry information security requirements. These systems provide policy rules and guidelines that the Policy Engine can incorporate into its decision-making process.
Threat Intelligence Feeds:
Integrating internal and external threat intelligence feeds is essential for staying informed about newly discovered attacks, vulnerabilities, and emerging threats. The Policy Engine can leverage this information to deny access requests from compromised or potentially malicious sources, enhancing the overall security posture of the ZTA.
Network and System Activity Logs:
Collecting and analyzing network traffic logs, resource access actions, and other system events provide real-time feedback on the security posture of the enterprise's information systems. This data can be used by the Policy Engine to detect anomalous behavior patterns and adjust access decisions accordingly.
Data Access Policies:
Data access policies are a crucial component of a Zero Trust Architecture (ZTA) implementation. These policies define the rules and attributes that govern access to enterprise resources, ensuring that only authorized subjects and assets can access data and services based on their defined mission roles and needs. Data access policies should be developed in collaboration with data custodians (those responsible for the data) and business process owners (those responsible for the mission). These policies should take into account the sensitivity and criticality of the data, as well as the specific access requirements for different roles and workflows within the organization.
Public Key Infrastructure (PKI):
A robust enterprise PKI is essential for generating and managing digital certificates used for authentication and encryption within a ZTA. The PKI system issues certificates to resources, subjects, services, and applications, enabling secure communication and identity verification. Integrating the enterprise PKI with the broader Federal PKI or other external certificate authorities can facilitate interoperability and trust relationships with external entities.
Identity Management System:
An identity management system is responsible for creating, storing, and managing enterprise user accounts and identity records. This system contains critical information about subjects, such as names, email addresses, certificates, roles, access attributes, and assigned assets. The Policy Engine relies on this system to authenticate and authorize subjects based on their identities and associated privileges. Additionally, the identity management system may be part of a larger federated community, enabling collaboration with non-enterprise users or assets.
Security Information and Event Management (SIEM) System:
A SIEM system consolidates security-centric information from various sources, enabling analysis and refinement of policies based on identified threats or potential attacks. The insights gained from the SIEM system can help the Policy Engine make more informed and proactive access decisions.
By integrating these external components into the ZTA implementation, organizations can leverage a comprehensive set of information sources to support the Policy Engine's decision-making process. This integration ensures that access decisions are based on real-time data about asset posture, threat intelligence, compliance requirements, and observed network activity, ultimately enhancing the overall effectiveness and adaptability of the Zero Trust Architecture.
Implementation Challenges and Considerations
Adopting a Zero Trust Architecture (ZTA) introduces several implementation challenges and considerations that organizations must address to ensure a successful transition and maintain an effective security posture. While ZTA offers enhanced protection against threats such as lateral movement and data breaches, its implementation requires careful planning and a planned approach to mitigate potential risks and issues.
Following are some of the major line items that need to be planned for along with the best practices guidelines to work around those.
Network Visibility and Monitoring:
One of the challenges in implementing ZTA is ensuring comprehensive visibility into network traffic, especially encrypted or opaque traffic from non-enterprise assets or applications resistant to passive monitoring. Organizations may need to employ advanced techniques like machine learning to analyze metadata and detect potential threats when deep packet inspection is not feasible.
Credential Management and Insider Threats:
While ZTA reduces the risk of lateral movement by compromised accounts, it does not eliminate the threat of stolen credentials or insider attacks. Robust credential management, multi-factor authentication, and contextual trust algorithms that detect anomalous access patterns are crucial to mitigate these risks.
Vendor Lock-in and Proprietary Formats:
The current ZTA ecosystem lacks standardization, with vendors relying heavily on proprietary APIs and data formats. This can lead to vendor lock-in, interoperability issues, and challenges in migrating between solutions. Adopting open standards and protocols can help mitigate this risk.
Non-Person Entity (NPE) Authentication:
As organizations increasingly employ automated agents, AI, and other software-based entities for security and administration tasks, there is a need to establish robust authentication mechanisms for these NPEs within the ZTA framework. Ensuring secure interactions between NPEs and ZTA components is essential to prevent potential misuse or compromise.
Resilience and Business Continuity:
The reliance on multiple interconnected components in a ZTA environment introduces potential single points of failure. Organizations must ensure the scalability and resilience of critical components like the Policy Engine and Policy Administrator to maintain availability and prevent disruptions to business processes.
User Experience and Training:
Implementing ZTA may introduce additional authentication steps or modify existing workflows, potentially leading to user frustration or security fatigue. Effective user training, streamlined processes, and continuous monitoring of user experience are necessary to maintain productivity and adoption.
Privacy and Compliance Considerations:
ZTA principles, such as continuous monitoring and traffic inspection, may raise privacy concerns or introduce compliance challenges related to data protection regulations. Organizations should leverage frameworks like the NIST Privacy Framework to identify and mitigate potential risks while maintaining compliance.
By proactively addressing these challenges and considerations, organizations can develop a comprehensive strategy for successfully implementing and maintaining a Zero Trust Architecture that aligns with their business objectives, security requirements, and regulatory obligations.
Conclusion
Implementing a Zero Trust Network Architecture requires a holistic approach that encompasses identity, device trust, network segmentation, and continuous monitoring. By following the NIST framework and focusing on protecting your most critical assets, organizations can significantly enhance their security posture. Remember that Zero Trust is not a one-time implementation but an ongoing process of improvement and adaptation. Regularly assess and update your ZTNA strategy to address evolving threats and technological advancements.
References
- Zero Trust Architecture - NIST Special Publication 800-207
- Getting Started with Zero Trust Access Management
Related Posts
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.


Comments (0)
No comment